Earlier this year, Umbraco released a security advisory and patches for multiple access control issues in the core CMS. As part of our work on the Umbraco Community Security and Privacy Team, we got to thinking about how we might help Umbraco developers to detect similar issues in their own applications and packages, so that they can address them before it becomes a problem.
TL;DR: We built a dashboard to allow you to see an overview of all of the controller actions and API methods in your application along with the authorization policies applied to them. The package is still in development, but we’ve released a preview to NuGet and published the source code on GitHub.
What are broken access controls?
Broken access controls were the most prominent web application security risk according to the OWASP Top 10 for 2021 (up from the fifth position in 2017):
Access control enforces policy such that users cannot act outside of their intended permissions. Failures typically lead to unauthorized information disclosure, modification, or destruction of all data or performing a business function outside the user’s limits.
In ASP.NET and Umbraco applications these kinds of issues often arise due to
incorrect or missing [Authorize]
attributes on controllers and action methods, or using
[AllowAnonymous]
in the wrong places. When these attributes are not applied properly it can lead
to APIs being exposed to attackers.
Code review
Something we like to do when Umbraco security releases come out is compare the source code between versions. You can do this easily on GitHub yourself. For example, here is a comparison between Umbraco 15.2.2 and 15.2.3.
As we can see, the patch in this case was quite simply to add some [Authorize]
attributes to various controllers. For example, the TreeAccessDataTypes policy
was applied to the DataTypeControllerBase class (and therefore will apply to
any classes that inherit from it):
+[Authorize(Policy = AuthorizationPolicies.TreeAccessDataTypes)]
public class CreateDataTypeController : DataTypeControllerBaseWith that in mind, we wanted to develop something to help developers spot when these attributes are missing or misconfigured without having to review every controller’s source code manually. The result is the Auth Policy Browser package.
Features
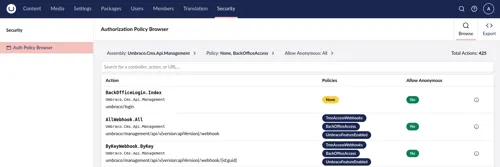
Once installed, the package adds a new Security section to the backoffice. The
main dashboard allows users to browse through all the actions that were found
in the application at runtime (for anyone interested, this information comes from the
IActionDescriptorCollectionProvider
interface).
It’s possible to filter the actions by the assembly they are defined in, the
policies applied to them with [Authorize] attributes, and whether
[AllowAnonymous] is applied:
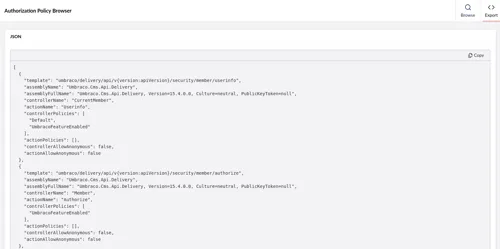
The raw data can also be exported to JSON, in case you want to analyse it in Excel or another program (we’d be interested to hear use cases, if any):
What to look out for
Particular attention should be paid to any actions that might allow anonymous
requests (i.e., those with [AllowAnonymous] attributes), and those without any
policies at all. Of course, some actions are supposed to allow anonymous
requests, but if your API method is only meant to be called by users who are
logged into the backoffice (for example), then it should probably have some
policies in place.
The policies themselves should also be reviewed to ensure that they are
appropriate for the API/action method in question. For example, if your API
should only be called by users with access to the Umbraco Settings section,
then it should have the SectionAccessSettings policy applied. In fact, we
came across this exact issue in the package itself during development (we
identified the issue using the dashboard!).
It should be noted that this package currently only looks at the
ASP.NET [Authorize] and [AllowAnonymous] attributes
and therefore will not account for any custom authorization logic that may
exist in an application. We’d be interested to know if there are other
attributes we should look at or any other information that would be useful to
show on the dashboard.
If you find a security issue
As mentioned, with this package you can see all actions across all assemblies that are loaded at runtime, including the Umbraco core CMS and any third-party packages you have installed.
If you find any authorization issues in the core CMS or packages, please disclose them responsibly following Umbraco’s guidance on how to report a vulnerability.
Contributing
We welcome contributions to the package via GitHub issues and pull requests. Check out the repo here: https://github.com/stvnhrlnd/Umbraco.Community.Security.AuthPolicyBrowser.
Web Hacking 101 Workshop (sales pitch #1)
We’re putting together a workshop for this year’s Umbraco Codegarden conference where we’ll look at how to detect, exploit, and fix common web application security vulnerabilities like broken access controls. We hope to see some of you there - it should be a lot of fun!
And if you can’t make it, don’t worry, the course materials will be made free and open sourced straight after the workshop.
Our Software Security Services (sales pitch #2)
We are also pleased to be able to offer our software security consultancy services to any organisations interested in improving their security posture.
We have many years of experience in both building and breaking software applications. We can help with penetration testing, source code review, and guidance for developers on how to write more secure code. If this is of interest to you, feel free to get in touch.